There I was in my ‘kerchief and my cap, settling down for a long winter’s nap. And then log4j happened and all hell broke loose…
To take my mind off of things, I completed about half of the 2021 SANS Holiday Hack Challenge. There are often multiple ways to solve the challenges, and I like to compare notes. I decided to write about the ones I was able to complete.
Exif Metadata
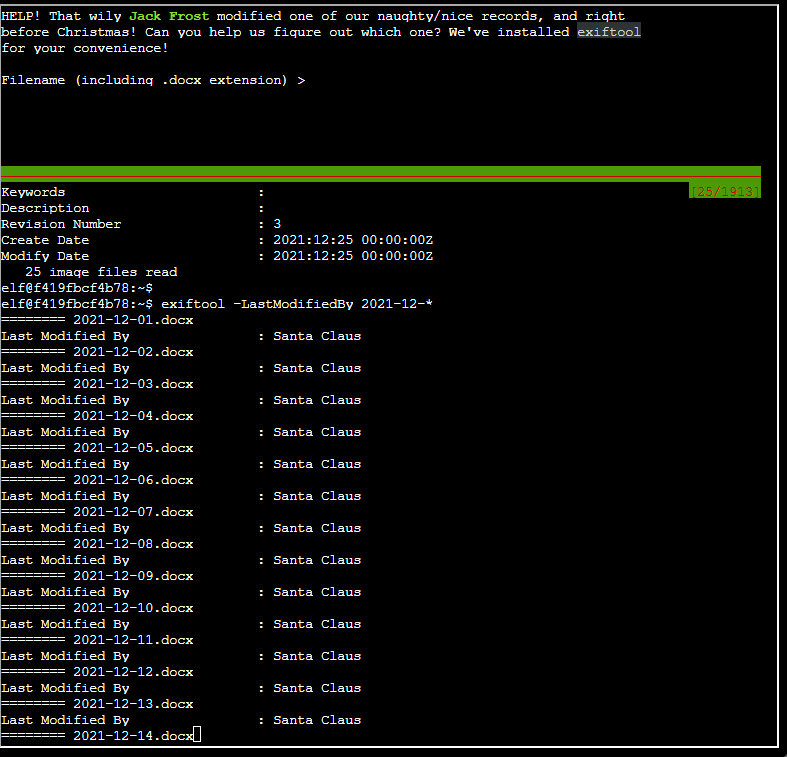
This was any easy one, and was located in the outside patio of Santa’s castle. I was given a Linux command line and the task was to discover which file has been tampered with using the exiftool command.
I entered the command exiftool -LastModifiedBy 2021-12-* to find the user who last modified all of the files, and found the file that was modified by “Jack Frost”.

Grepping for Gold
This challenge was located outside of Frost Tower. I was given a large nmap scan file and had to answer a series of questions about the data.
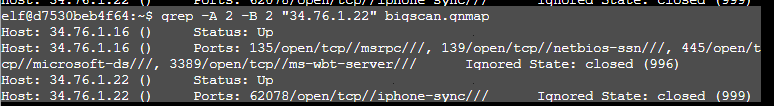
The first 2 questions were fairly straight forward, I used grep -A 2 -B 2 to show 2 lines before and after my search for the IP addresses, because I wasn’t sure how the data was formatted.
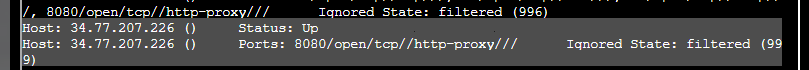
For question 3 I did grep "Up" bigscan.gnmap | wc -l to see how many instances of the string “Up” there were in the data.
Now it started to get more difficult. For question 4, I initially tried using awk to separate out all of the port numbers and then grep them and count them, but my awk syntax was wrong and I wasn’t actually pulling all of the instances of the ports on a host, just the first instance/column:
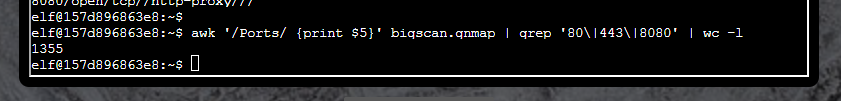
I Googled some syntax and used extended grep to find the answer:

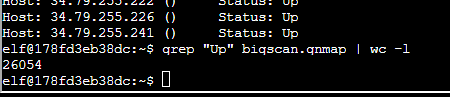
On to question 5. If I put in the command awk '/Host/' bigscan.gnmap I saw that an IP address usually appears twice, once for when it’s “Up” and once for when it has ports open:
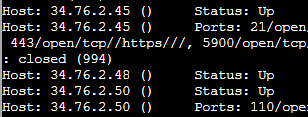
So all I needed to do was find the IP addresses that only appeared once, and those would be the ones that were “Up” but had no ports open:

I started by printing out all of the IP address columns. Then I used the uniq command to calculate if that address appeared once or twice, and then 1 or 2 would be prepended to the beginning of each line, along with a tab before the number. Then I used sed to take out the tab, grepped the lines that began with 1, and then counted those with the wc command. It wasn’t the obvious solution, but it worked:
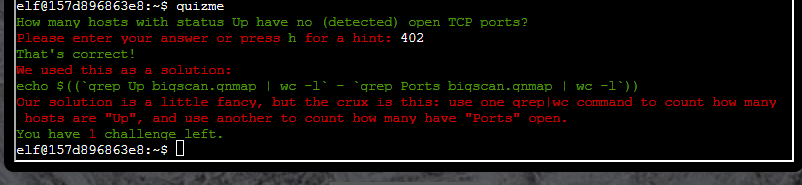
For the last question I used the following command:
grep "open" bigscan.gnmap | awk '{ print NF, $0 }' | sort -r | cut -d " " -f 1-3 | less
First I used grep to print out any line with the string “open” in it. Then I used awk to calculate the number of columns per line, essentially telling me the length of the line. This awk command also prepends the number of columns to the beginning of each line. Then I sorted those and cut the output down to a format where I could see what IP addresses had the longest lines:
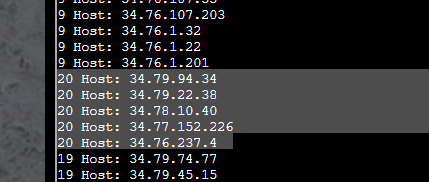
Then I grepped how many times the string “open” appeared with those addresses, and found it was not more than 12:
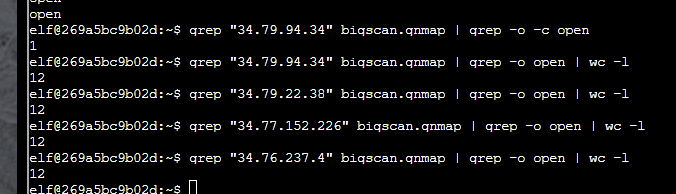
Again, not the obvious or easiest answer, but still correct:
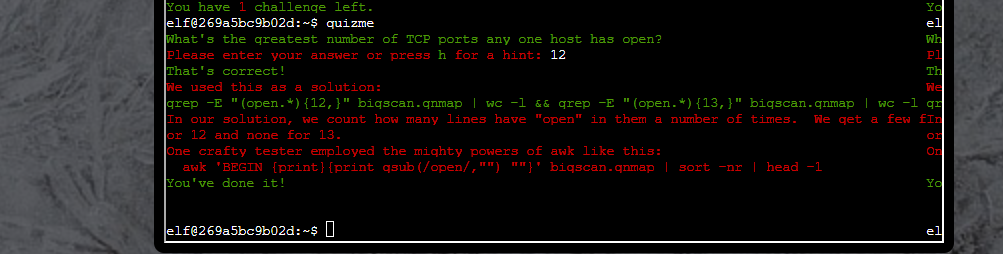
Sometimes I’m not sure how or why my brain comes up with these solutions.
Hacking Frosty Slots
This challenge was right as you enter Frost Tower.
It takes you to a separate URL where you can play a slot machine game in Jack Frost’s casino. The goal of the challenge is to find a way to hack the machine to pay out credits.
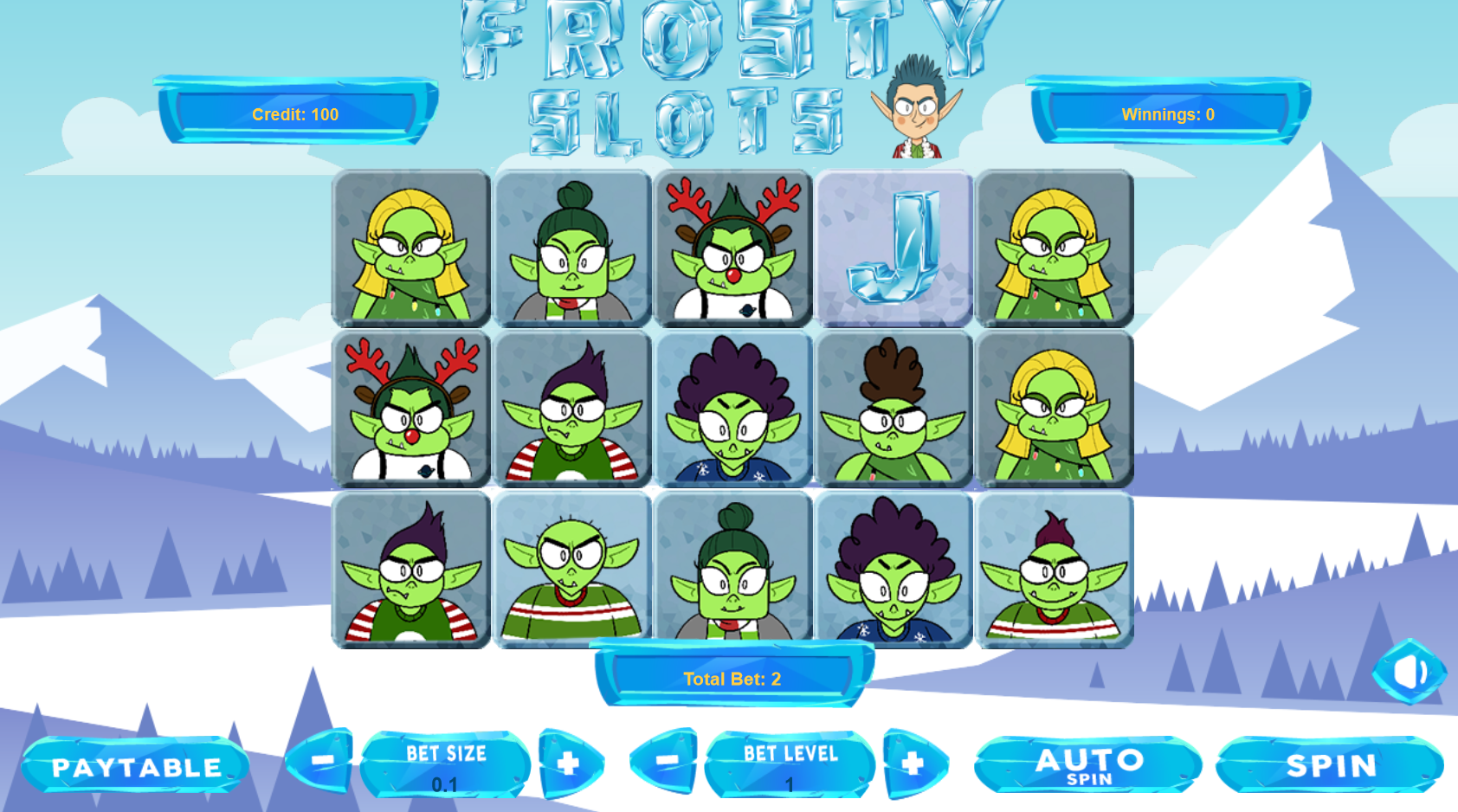
I fired up BurpSuite and took a look at some of the web traffic. When I did one bet I could see I was posting 3 variables. The betamount variable was how many credits I was betting, the numline variable was the number of lines I was betting on, and the cpl variable appeared to be the cost per line.
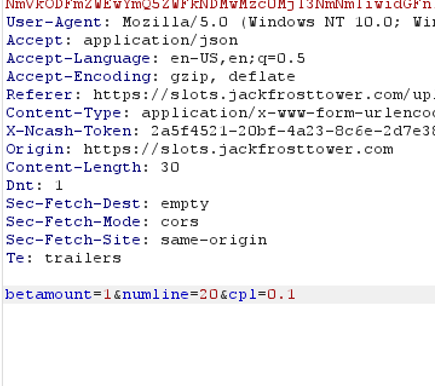
The server then responded with some JSON data, with a number of different values:
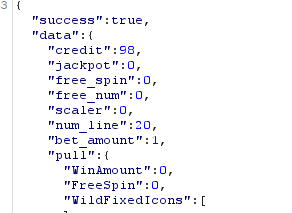
First, I tried to see if it would take any of those JSON values if I sent them:
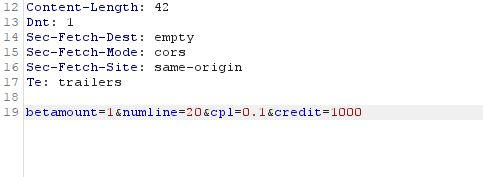
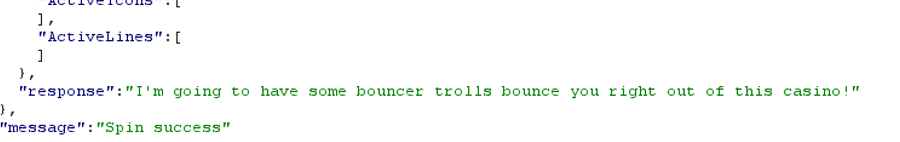
But that didn’t work. Then I tried changing the betamount variable to a negative amount and I got a message telling me no:

Then I tried changing the cpl variable to a negative number and that went through:

When you do that you get a response with a threatening message from casino security, and that’s the answer to the challenge: