I’ve been busy with some training at work, but wanted to start posting about some HackTheBox challenges I’ve been doing. I used a basic Kali VM. This challenge was particularly interesting for me, because I ended up getting a false positive while using the password cracker John the Ripper. I’m not sure how or why it happened, but somehow I did it. The challenge:
Can you find a way to login as the administrator of the website and free nginxatsu?
When I visited the IP address and port number there was a page that looked like this:

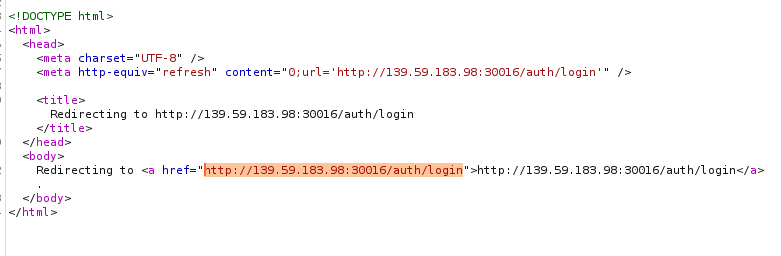
The first thing I noticed when examining the code on the site was that I was being redirected to /auth/login:
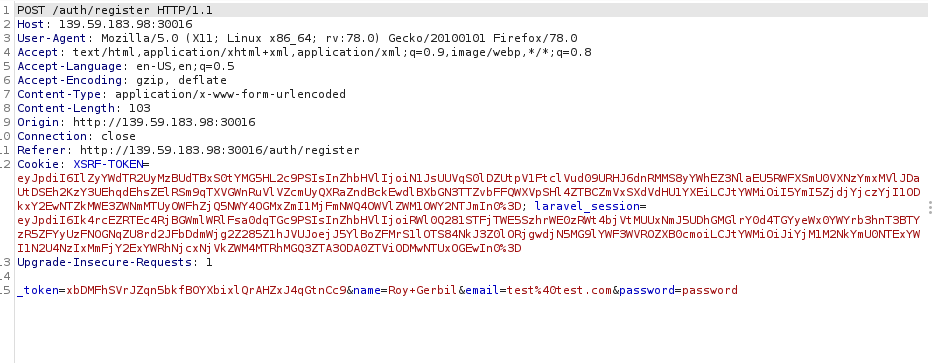
I decided to register a new user and see what that looked like. I did that successfully. I attempted to decode some of the cookie, but didn’t really find anything of interest:
Once I was logged in as that user, I saw a page with a form where I could submit input. This would generate a nginx configuration file.
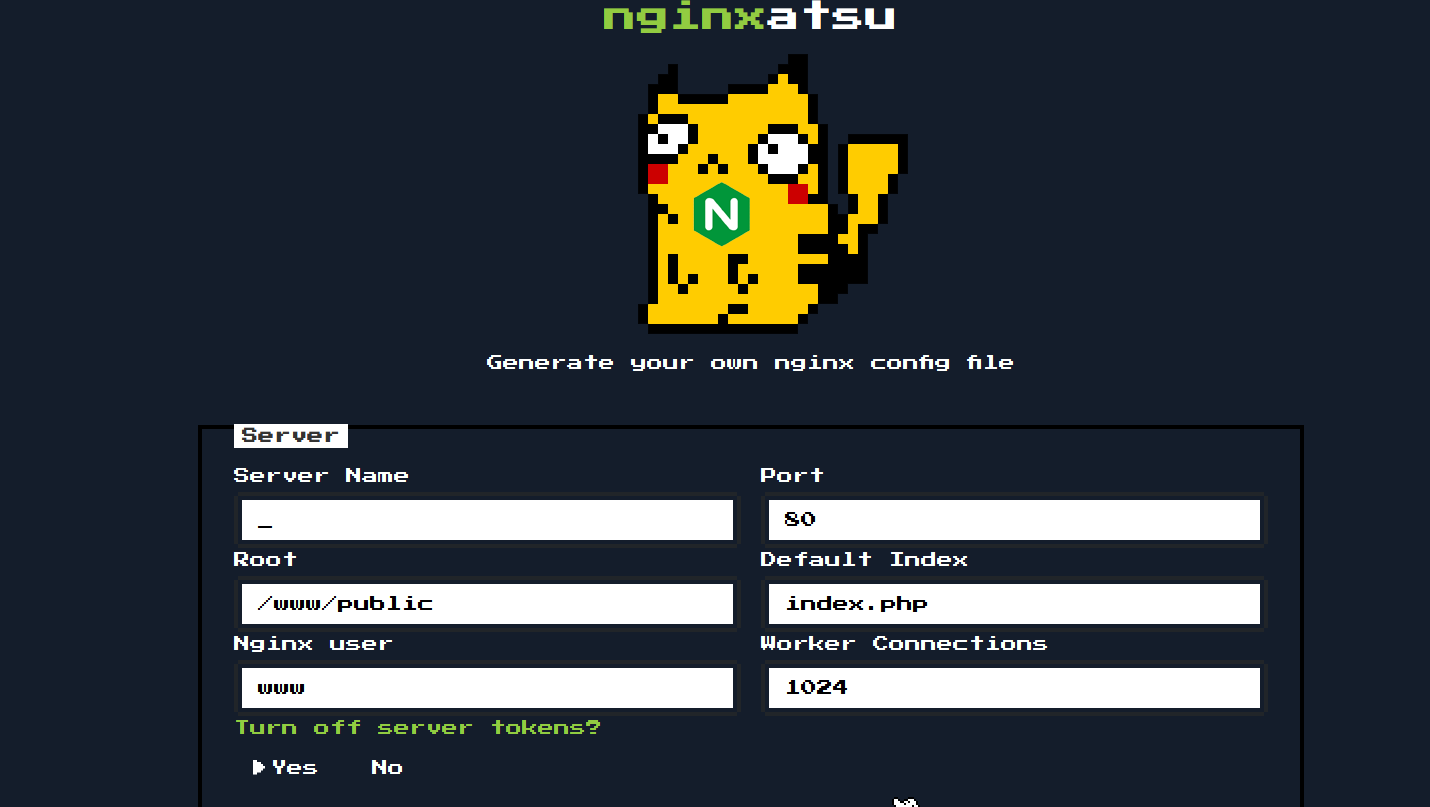
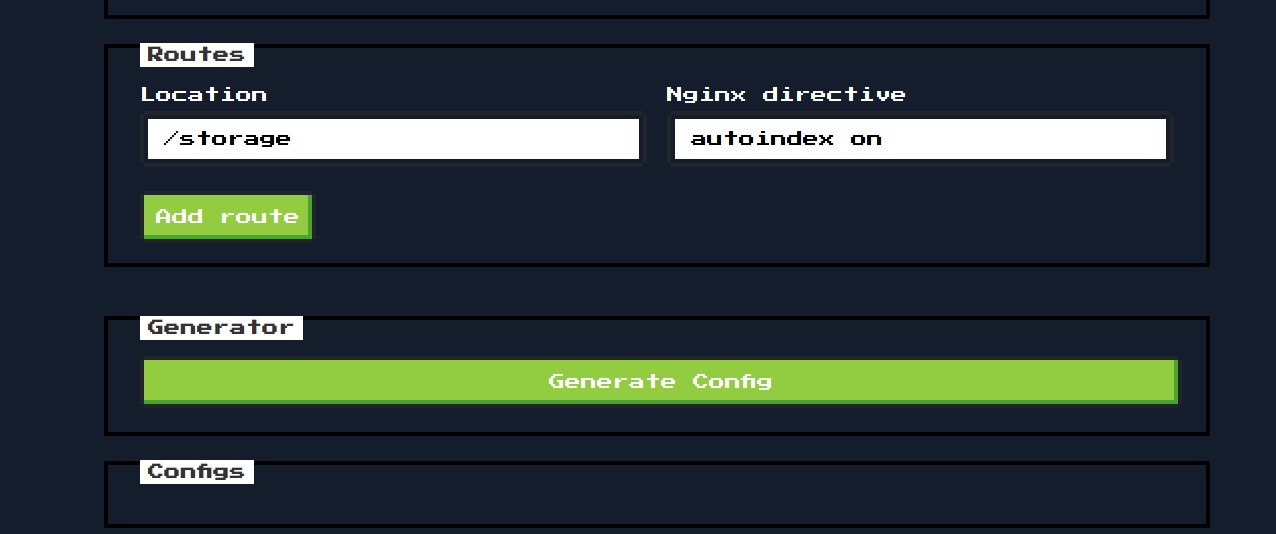
I wanted to see what happened when I put in a server name, so I put in “gumby” in the “Server Name” field, and it responded by creating a new icon to click on called “51”. Burp showed some JSON object details and a 201 response code, which meant a resource was created.
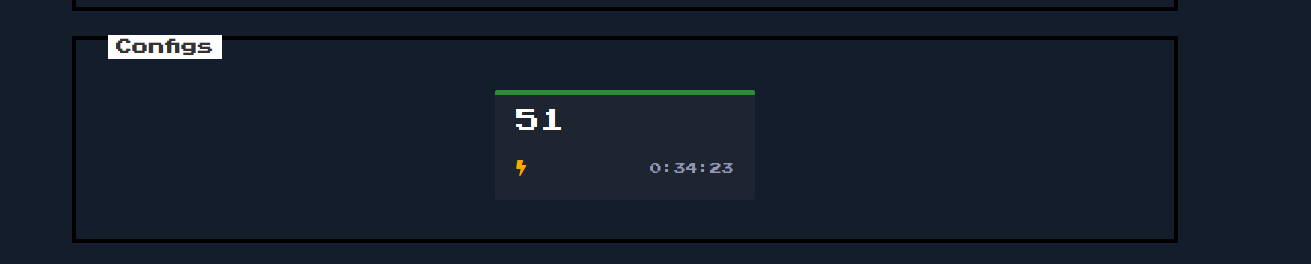


When I clicked on “51” it showed a nginx configuration file:


Hmmmmmmm. That comment about the /storage directory was interesting. I looked a bit more into nginx configurations files, since I had no experience with them. What did those references to “location” in the file mean anyway? After some reading I learned it was part of something called the server context, which was part of the HTTP context, which explained the curly bracket hierarchy.
So based off of that info, and the fact that the file was designating a /storage directory with auto indexing that was turned on I went to http://139.59.183.98:30016/storage/ and found multiple files:
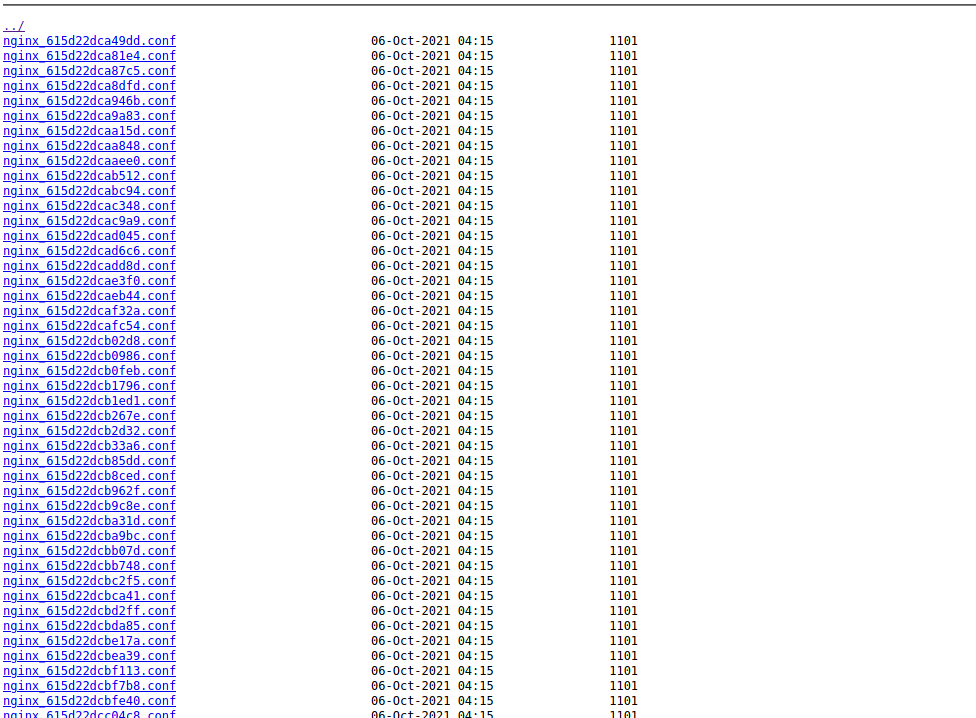
There were tons of .conf files, but I noticed a tar.gz file and downloaded that:
I tried decompressing and extracting it, but apparently it was only pretending to be compressed.
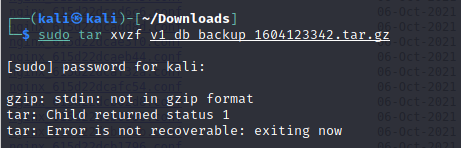
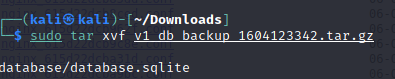
Well look at that! It’s an SQLite database. After looking at some of the tables in whatever GUI-friendly database program Kali had installed, I found the useful information for what I believed to be the admin user:
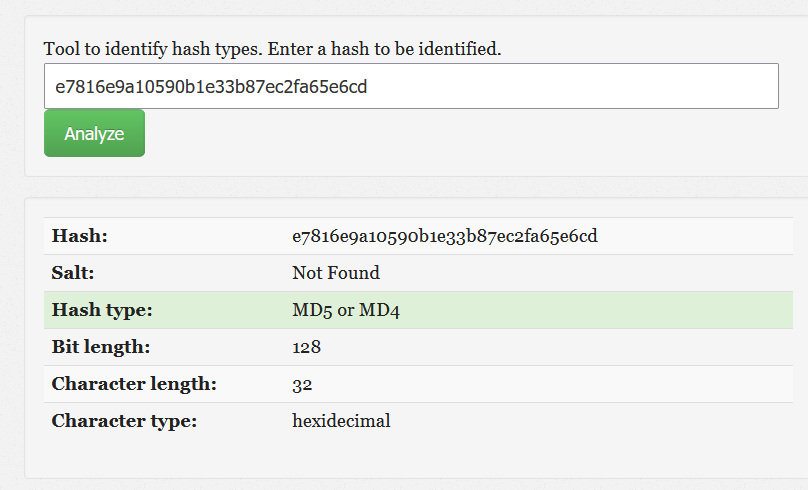
Password: e7816e9a10590b1e33b87ec2fa65e6cd
I decided to do some analysis on the user hash. It seemed to fall into the MD4/MD5 category, and no salting was detected, so that was good news.

I started up John and tried to crack the hash, first using the default options, and then using the rockyou.txt password list after the default run failed.

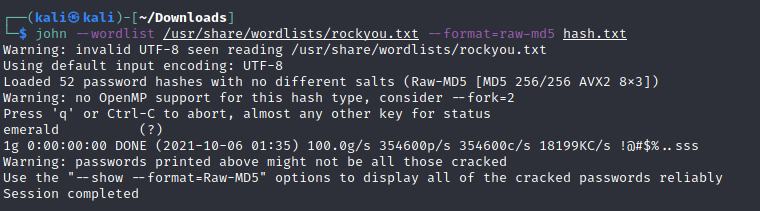
And it looks like the password is “emerald”! So I went to http://139.59.183.98:30016/auth/login and entered in the email and password and… it did not work. I used a MD5 hash generator and put in the word “emerald” and it did not match the hash I had. John was wrong, wrong, wrong. Either that, or I used it wrong.
As a backup plan I decided to use CrackStation for all the user hashes I had from the SQL database, and that did the trick for getting the admin password. CrackStation also identified the hash as MD5 so I’m not sure what went wrong.
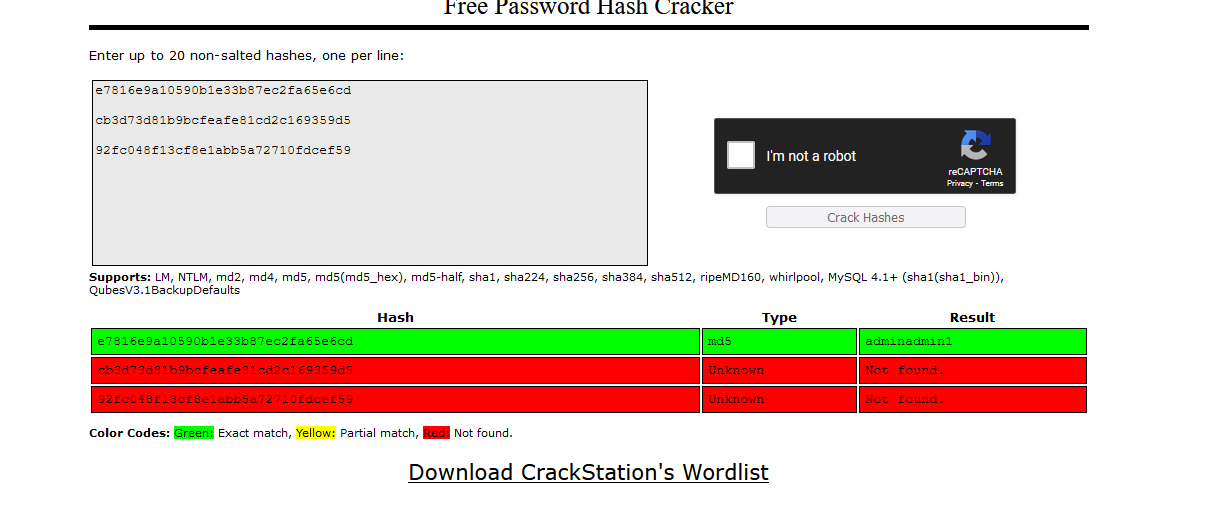
I logged in with the “adminadmin1” password and got the flag.
