Another Juice Shop challenge I really enjoyed recently was Two Factor Authentication.
Here was the question:
Solve the 2FA challenge for user “wurstbrot”. (Disabling, bypassing or overwriting his 2FA settings does not count as a solution)
A more detailed explanation stated:
In the Juice Shop one customer was very security-aware and set up 2FA for his account. He goes by the hilarious username wurstbrot.
As always, first learn how the feature under attack is used and behaves under normal conditions.
Make sure you understand how 2FA with TOTP (time-based one-time password) works and which part of it is the critically sensitive one.
Solving the challenge Retrieve a list of all user credentials via SQL Injection before tackling this one will definitely help. But it will not carry you all the way.
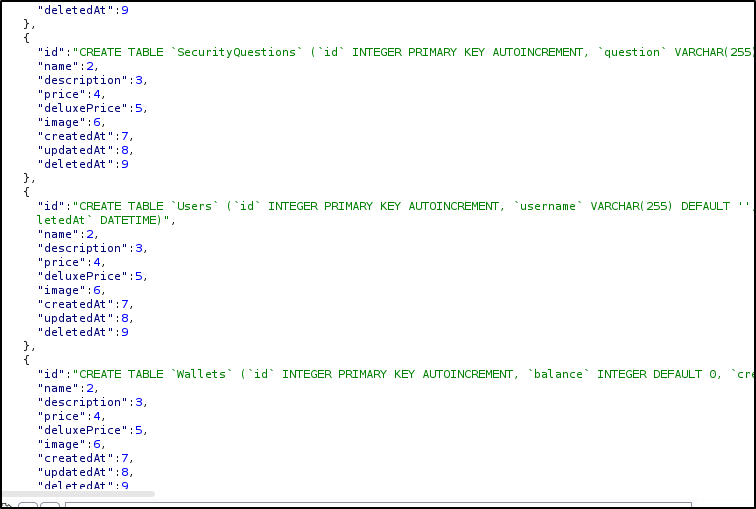
I felt like I had a fairly good grasp on TOTP 2FA and how it worked. And I remembered there was a column related to TOTP in the Users table when I completed another challenge that dumped the website’s database (SQLite) schema. So I used the same tactic in Burp Suite to see all of the columns that existed in the Users table:
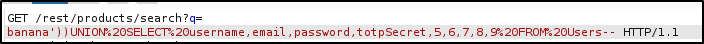
And in that table there was a column called totpSecret, which looked promising. So I used another injection request to see what data was there:
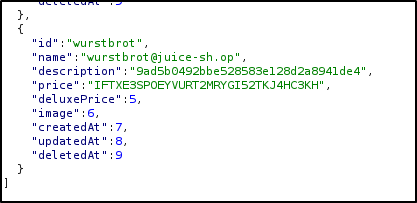
And sure enough, when I got to the user “wurstbrot” there was a TOTP setup key there in plain text.
TOTP setup keys can be used in lieu of a camera on a phone taking a picture of a QR code with an authentication app. All I had to do was put that key in Google Authenticator to get access to wurstbrot’s TOTPs.
I then used some more SQL magic from a previous challenge to bypass the user’s account password and then when it prompted me for the 2FA code I entered that in as well.
And with that the challenge was solved. The lesson here is that 2FA with a 3rd party authenticator app can be a very effective way to secure an account… unless you leave the setup key in plain text where an attacker can get to it.